In this section, we will learn how to protect from delivery methods. We are going to use tools like XArp, or static ARP table to prevent a man-in-the-middle attack, and avoid networks we don't know. Another precaution is to ensure that we are using the HTTPs when we download updates. This will reduce the risk of downloading a fake update.
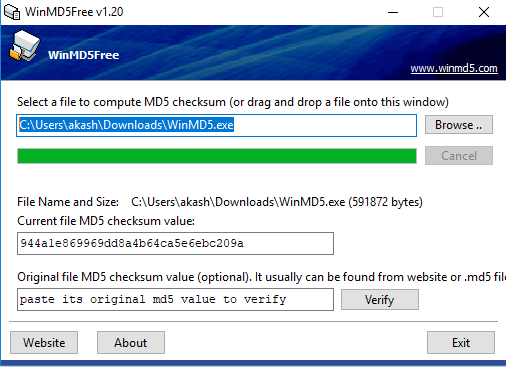
We are going to learn another tool that is useful, which is WinMD5. This program will alert us when the signature or checksum of the file has been modified in any way, which indicates that the file is not the original file. To check, we are going to download and run WinMD5, where we can compare signature and checksum for a file. If the values of signature and checksum are same, the file is safe. We can download WinMD5 using the following link:
http://www.winmd5.com/
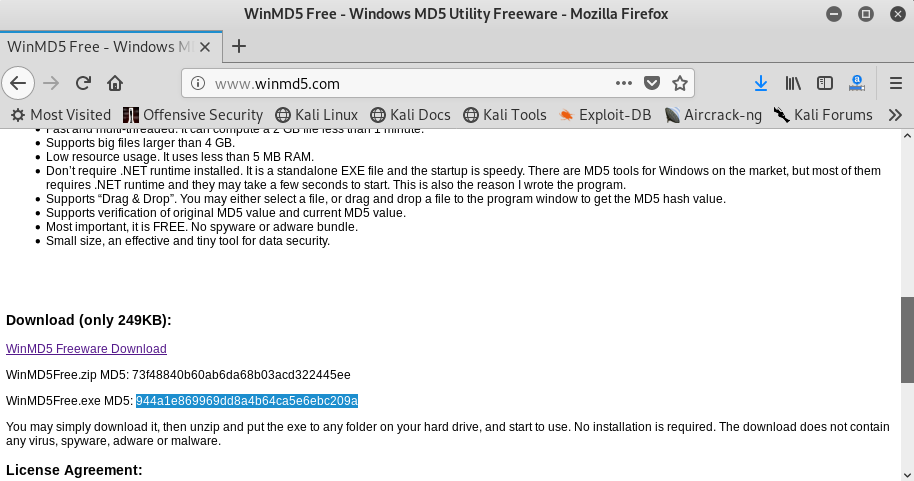
In the following screenshot, the highlighted part shows the signature of this tool:
Now, if we go on Browse, it will show us the signature files. In this example, we are going to select the downloaded file for this tool itself. Now, we are going to compare this signature with the signature at the website, and we can see in the following screenshot that both the signatures are same. This means that the tool has not modified and downloaded from the website: